Malware campaigns hit North Korea following nuclear ICBM tests

Researchers have stitched together two sophisticated malware campaigns that are targeting North Korea, raising suspicion over counteractions tied to the country’s aggressive weapons testing.
Cybersecurity researchers from Cylance released a report Tuesday asserting that Konni, a recently discovered but long active family of remote access trojans, was used in a malware campaign targeting North Korea shortly after a July 3 missile test. It marks the fifth known Konni campaign in three years and the third in 2017.
This follows similar reports from the firm Talos that showed a Konni campaign launched just a day after missile tests on July 4.
In addition to the malware campaign, Cylance is connecting Konni to a hacking group known as DarkHotel. Just a few days after the July ICBM test, a whitepaper by the cybersecurity firm BitDefender reported a new campaign from DarkHotel, a group that has successfully targeted businesses for a decade through security holes in Wi-Fi infrastructure at hotels around the world.
The July campaign, called “Inexsmar,” stands out: DarkHotel appears to be targeting political figures instead of businesses, and uses a payload mechanism distinct from the zero-day exploits and social engineering the group is known for.
The latest DarkHotel campaign targeted North Koreans, among other victims.
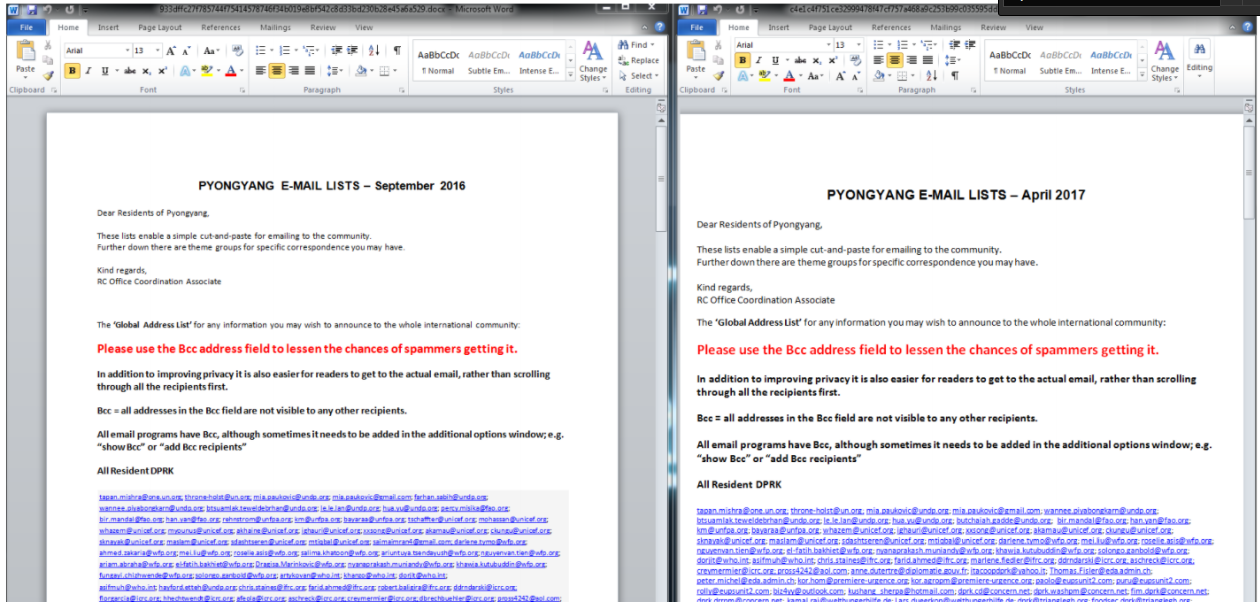
Inexsmar includes a malicious malware dropper titled “Pyongyang Directory Group email SEPTEMBER 2016 RC_OFFICE_Coordination_Associatewxcod.scr” that is notably similar to a document used in Konni campaigns titled “Pyongyang Directory Group email April 2017 RC_Office_Coordination_Associate.scr.”
Both include phone numbers, email addresses and contact information for people from institutions including the United Nations, UNICEF, and North Korean embassies.
The two files are side by side below:
Cylance
Cylance researchers do not draw any explicit conclusions about links beyond what’s been found here. Instead, they raise the question for future research, particularly if Konni and DarkHotel may be connected.
The first known Konni campaign took place in 2014, followed by action in 2016. The malware family has been developed further with new additions on every campaign.
Konni is a purpose-built Remote Access Trojan with anti-analysis, social engineering and intelligence gathering features, Cylance researchers write. It’s distributed through phishing, attempts to stay hidden during execution and then gives attackers massive visibility into a target’s network and machine — including key logging and screen captures.
“Attacks Leveraging Social Engineering techniques and Intelligence Gathering can be devastating for many
companies,” the researchers wrote, “as these attacks target human being’s emotions of trust and can lead to total take over.”
North Korea is increasingly active in the cyber domain. The country’s hackers came close to breaking into Hillary Clinton’s presidential campaign. Groups like the Lazarus Group, widely credited to Pyongyang, have been behind cyberattacks that have resulted in the theft of millions of dollars.
North Korea is seen by several Western intelligence agencies as the country behind this year’s WannaCry ransomware attacks.






