U.S. warns of ’emerging’ global cyber-espionage campaign by Chinese hackers

An “emerging” international cyber-espionage campaign by a group with suspected ties to the Chinese government is affecting a growing number of companies globally, according to a warning from the U.S. government.
Cybersecurity researchers and intelligence analysts have been tracking the hacker group known as APT10 or MenuPass Group since at least 2009. In the past, the group has targeted construction, engineering, aerospace and telecom companies as well as government agencies in the U.S., Europe and Japan. APT10’s past activity suggests it acts in “support of Chinese national security goals, including acquiring valuable military and intelligence information as well as the theft of confidential business data to support Chinese corporations,” according to cybersecurity firm FireEye, which has extensively monitored and studied the group.
The U.S. National Cybersecurity and Communications Integration Center continues to review APT10’s recent activity and said it is working with victims “across different sectors,” according to a U.S. Computer Emergency Readiness Team incident report issued Thursday. NCCIC is the Department of Homeland Security agency focused on protecting U.S. critical infrastructure from hackers.
US-CERT will typically push out an incident report after a U.S. company is impacted by a specific cyberthreat. CyberScoop confirmed that at least one major U.S.-based IT service provider was compromised by APT10 in recent months. It remains unclear if or to what extent confidential data was exfiltrated from this victim.
The US-CERT report references recent, relevant research conducted by private sector firms, including BAE Systems, FireEye, PwC and Palo Alto Networks.
U.S. cybersecurity firms witnessed a surge in computer intrusions affiliated with APT10 last summer — beginning around June 2016 — subsequently leading to a wider spread of victims and the discovery of new hacking tools and other capabilities apparently used by the group.
APT10 continues to be active. Most of the group’s recent intrusions have begun with a carefully crafted phishing email, experts say.
“Over the last year, they’ve hacked into organizations in Scandinavia, Brazil, South Korea and Japan to do economic espionage and for national security purposes,” said John Hultquist, director of cyber espionage analysis at iSIGHT Partners. “IT service providers around the globe have also been hit, allowing APT10 to access a secondary group of victims — the service providers’ clients.”
Hultquist said that his team at iSight, a subsidiary of FireEye, has yet to see APT10 specifically conduct economic espionage against U.S. companies as part of the recent, global hacking campaign.
A recently uncovered, APT10-related data breach investigated by Palo Alto Networks found that APT10 targeted several different Japanese universities, pharmaceutical companies and manufacturing organizations last year.
Palo Alto Networks declined to answer questions concerning Thursday’s US-CERT incident report.
Joint research by PwC and BAE Systems published last month showed that APT10 was also involved in an operation to target managed IT service providers in the United Kingdom as a way to access intellectual property and other sensitive data stored by both the service providers themselves and their clients.
Digital forensic experts from Palo Alto Networks and FireEye were able to recover some evidence showing that the Chinese espionage group developed and deployed several new and unique backdoor implants, remote access trojans and booby-trapped email attachments in 2016 and 2017 to break into, take control and move laterally through targeted computer networks.
One of those hacking tools is an implant codenamed REDLEAVES, or BUGJUICE, which loads encrypted shell codes onto a compromised computer — giving the attacker the ability to find files, enumerate drives, exfiltrate data and take screenshots.
Because APT10 was able to successfully target numerous supply chain companies — firms that are typically integrated with other organizations’ technology infrastructures — the group’s conquest now poses a considerable threat to a wide range of different entities, explained Hultquist.
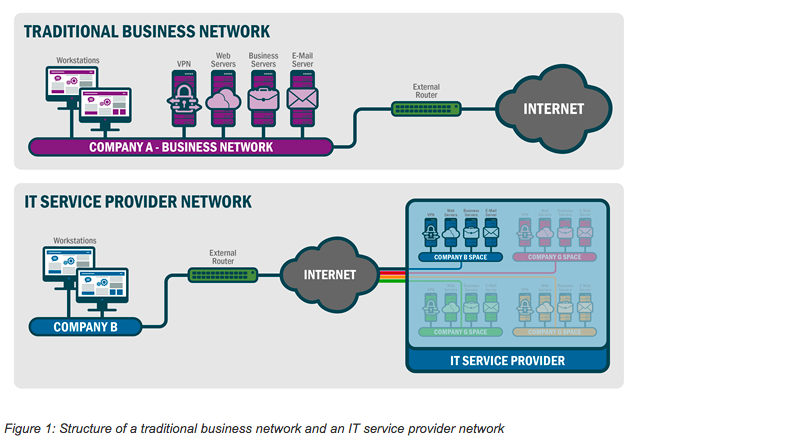
Graphic explaining the scope of APT10’s operation via US-CERT report
A DHS spokesperson did not respond to CyberScoop’s questions concerning related intrusions aimed at American companies.






