Spies used malware to eavesdrop on Ukrainian businesses and media, researchers say

Security researchers have found that a mysterious hacking group is spying on dozens of Ukrainian businesses by infecting their computers with highly sophisticated malware that allows for eavesdropping and data exfiltration.
The espionage campaign successfully compromised at least 70 victims, according to research published Wednesday by threat intelligence firm CyberX. Dubbed BugDrop, the clandestine hacking collective is believed to be well resourced, highly skilled and potentially backed by a nation-state.
“There’s been a lot of cyber activity in the Ukraine — but what makes this one stand out is its scale and the amount of human and logistical resources required to analyze such massive amounts of stolen data,” CyberX CTO and co-founder Nir Giller told CyberScoop.
A range of different business sectors were targeted by BugDrop in recent months, including critical infrastructure, media and Ukrainian research centers. The custom computer virus gives BugDrop the ability to capture sensitive information like audio recordings, screen shots, documents and device passwords.
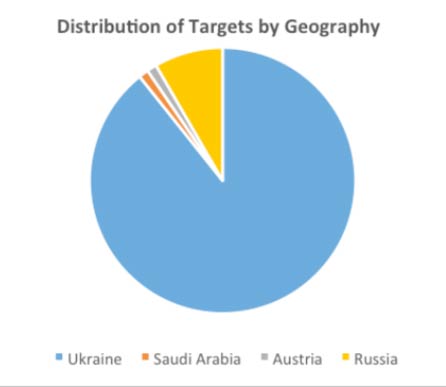
While most of the targets identified by CyberX are located in Ukraine, researchers also found fingerprints of BugDrop in several breaches that occurred in Russia, Saudi Arabia and Austria.
The spyware is typically distributed through email phishing attacks and malicious macros embedded in Microsoft Office attachments. Dialog boxes that pop up when the malicious Word document is opened by a victim are written in Ukrainian, though the original language of the document is Russian. The creator of the decoy document creator is named “Siada.”
Image of decoy word document, which shows information about Ukranian military personnel
When the malware-laden Word document is opened, hidden, malicious VB scripts start running in a temporary folder. The main downloader has low detection rates and carries a suspicious icon image — borrowing from a meme that is commonly shared by users of a Russian social media site.
“Given the high level of cyber activity in the Ukraine, this could be Russian-backed groups spying on Ukrainian targets or Ukrainian groups spying on pro-Russian separatist targets — or even organized cybercriminals offering their services to the highest bidder. We simply don’t know,” said Giller, a former security system engineer with the Israeli Defense Force.
Recently recovered evidence of BugDrop’s hacking tools and techniques share similarities with another, previously discovered group first uncovered by Slovakian IT security company ESET, named Groundbait.
The primary difference, however, between BugDrop and Groudbait lies in the fact that BugDrop boasts substantial capabilities that enable it to obfuscate its operations — making it more difficult for investigators to track the group down.
“This operation is distinguished by its use of Dropbox and free web hosting sites to maintain anonymity and its encryption of exfiltrated data,” Giller said, “attribution is notoriously difficult, with the added difficulty that skilled hackers can easily fake digital clues or evidence to throw people off their tail.”
BugDrop, for example, has shown the ability to deploy an advanced technique known as reflective DLL injection to effectively sidestep security verification procedures employed by Windows API. And by also encrypting the malicious code itself, the group was able to trick potential antivirus screening services and sandboxing mechanisms — because the malware could not be analyzed in transit.
CyberX’s research team reverse-engineered BugDrop’s signature malware to analyze its various components after they discovered the code in the wild. CyberX’s investigation took two months to complete.





