Google reveals sophisticated Italian spyware campaign targeting victims in Italy, Kazakhstan

The little-known Italian spyware firm RCS Labs worked with unnamed internet service providers to install malicious apps on targets’ phones in Italy and Kazakhstan, researchers with Google’s Threat Analysis Group said Thursday.
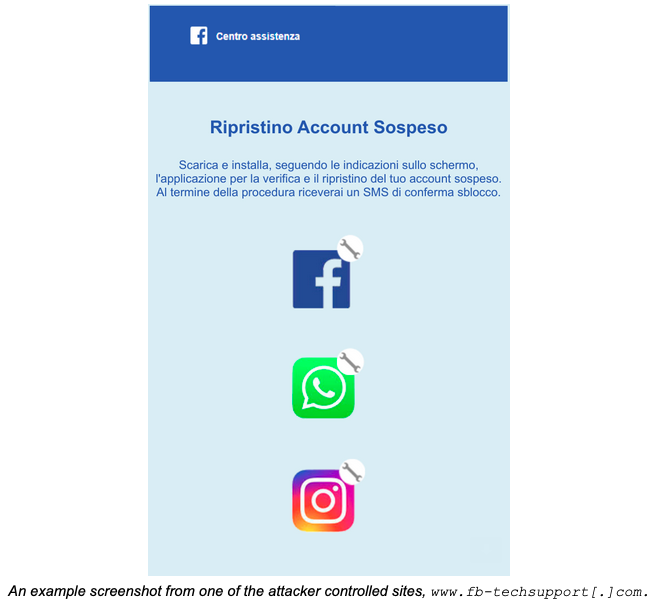
In some cases, where ISP involvement wasn’t possible, Google researchers said the firm sent fake warning messages to targets telling them to click a link to restore access to a popular messaging app. The link would then install a malicious version of the app, giving the firm’s customers access to the device.
“Our findings underscore the extent to which commercial surveillance vendors have proliferated capabilities historically only used by governments with the technical expertise to develop and operationalize exploits,” Google’s Benoit Sevens and Clement Lecigne researchers wrote. “This makes the Internet less safe and threatens the trust on which users depend.”
Ian Beer, a researcher Google’s Project Zero, which studies previously undisclosed hardware and software vulnerabilities, published a detailed analysis of the since-fixed iOS vulnerability the firm used in its fake mobile phone provider app. The memory corruption exploitation at work is akin to the FORCEDENTRY zero-click exploit exposed late last year and developed by Israel’s NSO Group, Beer wrote.
“Both reveal the stunning depth of attack surface available to the motivated hacker,” Beer wrote. “And both show that defensive security research still has a lot of work to do.”
NSO Group and another Israeli firm, Candiru, were added to the U.S. government’s entity list in November over concerns around their spyware being used to maliciously target civil society workers, journalists and activists.
The campaign targeted both iOS and Android devices, the Google researchers said. It’s not clear who was targeted in the campaign, or which RCS Labs clients were involved. Last week, cybersecurity firm Lookout published research that exposed spyware activity in Kazakhstan targeting Android devices with malware it dubbed “Hermit.” Lookout attributed the malware to RCS Labs and Tykelab Srl, “a telecommunications company we suspect to be operating as a front company.”
Lookout further alleged that Hermit was deployed by an entity of the national government in Kazakhstan. Hermit may have also been deployed in Syria and Italy, the company said, adding that RCS Labs has past connections to Italian spyware vendor HackingTeam, and that there are indications the company had worked in the past with governments in Pakistan, Chile, Mongolia, Bangladesh, Vietnam, Myanmar and Turkmenistan.
In a statement provided after publication, RCS Labs, based in Milan with affiliates in France and Spain, told CyberScoop that its products and services are provided to law enforcement agencies to combat serious crimes “in compliance with both national and European rules and regulations.”
“RCS Lab personnel are not exposed, nor participate in any activities conducted by the relevant customers,” the statement read. “RCS Lab strongly condemns any abuse or improper use of its products which are designed and produced with the intent of supporting the legal system in preventing and combating crime.”
On its website the company says it has been “providing Law Enforcement Agencies worldwide with cutting-edge technological solutions and technical support in the field of lawful interception for more than twenty years.” The company claims to be “the leading European provider of complete lawful interception services, with more than 10,000 intercepted targets handled daily in Europe alone.”
The Google researchers noted that while “use of surveillance technologies may be legal under national or international laws, they are often found to be used by governments for purposes antithetical to democratic values: targeting dissidents, journalists, human rights workers and opposition party politicians.”
The term “zero-day” refers to exploits that have been previously undisclosed, meaning vendors have had zero days to fix it. Seven of the nine zero-day exploits the Threat Analysis Group discovered in 2021 were developed by commercial providers and sold to and used by government-backed actors, the researchers wrote.
Google’s Threat Analysis Group is “actively tracking more than 30 vendors with varying levels of sophistication and public exposure selling exploits or surveillance capabilities to government-backed actors,” the researchers wrote.
The researchers concluded that “the commercial spyware industry is thriving and growing at a significant rate,” calling it a “trend that should be concerning to all Internet users.”
Updated, 6/24/22: to include a response from RCS Lab.






