Network size is no predictor of cyberattack readiness, penetration tests show

There is little predictable difference between the cybersecurity of IT networks in large companies as opposed to small ones, or between those from different business sectors, according to hackers for hire who try to break in to test defenses.
The penetration testers who work for security firm Rapid7 answered a questionnaire last quarter after 128 different engagements with a wide variety of companies. Rapid7 published the results Wednesday in a report called “Beneath the Hoodie.”
“You might expect a large, financial industry enterprise of over 1,000 employees would be better equipped to detect and defend against unwelcome attackers due to the security resources available and required by various compliance regimes and regulatory requirements. Or, you might believe that a small, online-only retail startup would be more nimble and more familiar with the threats facing their business,” wrote Director of Research Tod Beardsley, in a blog post.
But as it turns out, “detection and prevention rates are nearly identical between large and small enterprises, and no industry seemed to fare any better or worse when it came to successful compromises,” he wrote.
He says this is likely due to the fact that all companies use a mix of products from the same familiar vendors. “Thus, all networks tend to be vulnerable to the same common misconfigurations that have the same vulnerability profiles,” he wrote.
Just over two-thirds of the companies tested had websites with exploitable (i.e. unpatched) vulnerabilities — most commonly either either cross-site request forgery, clickjacking or cross-site scripting — that opened up their systems to hackers.
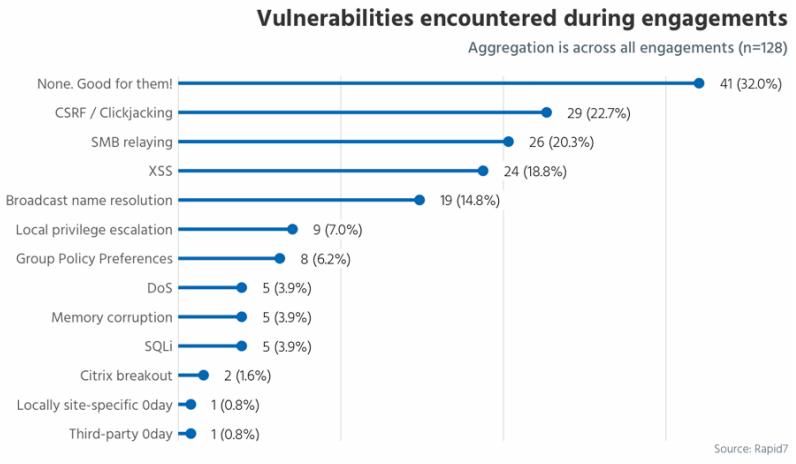
The same proportion, two-thirds, of the networks tested suffered from some kind of configuration error. Service misconfigurations and default account access were the most common, but other issues included no network segmentation, failing to enforce least privilege principles or a lack of password and patch management.
Although these are often thought of as “internal issues,” the report states that one or two of them “is oftentimes enough to traverse the (largely imaginary) boundary from ‘outside’ to ‘inside,’ and these issues should absolutely not be considered insider-only risks.”
Overall, the penetration testers successfully broke into the networks they were targeting just over 80 percent of the time, Rapid7 said, and more than two-thirds were never detected.






