Manufacturing companies got wrecked by cyber-spies last year, Verizon report says

Cyber-spies backed by nation-states were behind a majority of data breaches experienced by manufacturing companies in 2016, according to Verizon’s newly published 2017 Data Breach Investigations Report.
Verizon identified 620 data breach incidents in the manufacturing sector last year — of which 94 percent could be defined as “espionage” driven and attributable to “state-affiliated” actors.
Roughly 91 percent of material stolen in these breaches had been categorized as “secret,” relating to proprietary information owned solely by the victim.
Cybersecurity experts say hackers largely target the manufacturing industry in order to steal trade secrets, business plans and valuable intellectual property. Verizon defines cyber-espionage as incidents that include “unauthorized network or system access linked to state-affiliated actors and/or exhibiting the motive of espionage.”
“When you make stuff, there is always someone else who wants to make it better, or at least cheaper. A great way to make something cheaper is to let someone else pay for all of the R&D and then simply steal their intellectual property. With that in mind, it will probably be of no surprise that Cyber-Espionage is by far the most predominant pattern associated with breaches in Manufacturing,” the Verizon report reads.

Manufacturing companies are the top target for spies, according to Verizon
Prototypical of a government-backed hacking operation, most data breaches in the sector, according to Verizon, are highly targeted and narrowly focused on certain content that is stored by specific companies — rather than opportunistic, these breaches are well-planned and usually indicative of a longer term intelligence gathering effort.
Following years of damaging, cyber-enabled economic espionage, former U.S. President Barack Obama met with Chinese President Xi Jinping in late 2015 to discuss and agree to a diplomatic treaty. Since that agreement, cybersecurity firms that track Chinese hackers noticed a realizable decrease in economic espionage coming from Beijing. Nevertheless, the threat continues to exist in a global arena between other nations.
“Until recently, the bulk of Chinese cyber-espionage was attributed for the purpose of stealing information for their own corporations, notably manufacturing. In a global economy, goods can be produced anywhere and if you can steal the R&D behind those goods, an unethical company will always be able to undercut and win on price,” said John Bambenek, threat research manager at Fidelis Cybersecurity. “Further complicating the matter is that while manufacturing is increasingly high-tech, they often don’t have high security.”
Verizon found that most computer intrusions in the manufacturing industry begin with a well-crafted spear-phishing email, containing a malicious link or attachment, that is sent to a company employee. In such cases, malware is installed in the form of a backdoor or C2 after a booby-trapped attachment is opened, giving the attacker remote access to an internal computer.
Social engineering and malware-based cyberattacks combined for a whopping 73 percent of all data breaches in the manufacturing sector last year. Spies are known to favor email phishing techniques and using malware to compromise victims.
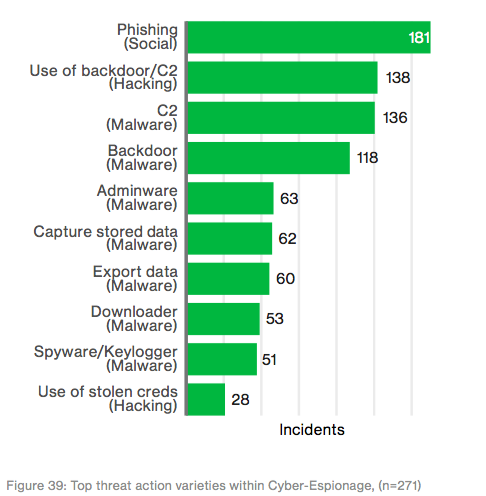
Techniques/methods used by cyber espionage groups — graph and data via verizon
In a broader context, Verizon claims that cyber-espionage groups were responsible for 289 confirmed data disclosures in 2016 alone across all sectors. Similar to past years, the unique state-affiliated, threat actor group accounted for a majority of the known breaches experienced by organizations in the government and manufacturing sectors.
“Unlike organized criminal groups, who are typically after directly monetizable data, state-affiliated actors are playing the long game and are more selective of their targets,” the report notes.
Capable, government-backed digital espionage groups are sometimes referred to as Advanced Persistent Threats, or APTs, by the cybersecurity research community — a reference that ties back to the ability of these attackers to gain and maintain access to a target network.
Some of the most high-profile cybersecurity storylines of 2016 involved APT groups attacking political organizations, including a breach at the Democratic National Committee eventually attributed to APT-28, a Russia-linked espionage group.






